The HY-VPN service offers university users access to services that are available only to the university’s perimeter network. This does not apply to all services available at the university. For example, certain software licence servers are not visible to the perimeter network and licence services they offer cannot be used. In some cases, this is due to a low number of licences, meaning that we have wanted to ensure that there are enough licences to internal university users.
Services obtained by different units, such as article and database services are not necessarily open to the perimeter network. If you would like to use such services, contact the unit responsible for the maintenance of the service to enquire about a possibility of opening the service to the perimeter network in order to make it accessible with the HY-VPN service.
The HY-VPN service is implemented with the openvpn software. It is available for all Linux distributions either via the distribution’s own package repository or by downloading the software package from the developers’ site and compiling it yourself.
Website for the software https://www.openvpn.net
Quick help
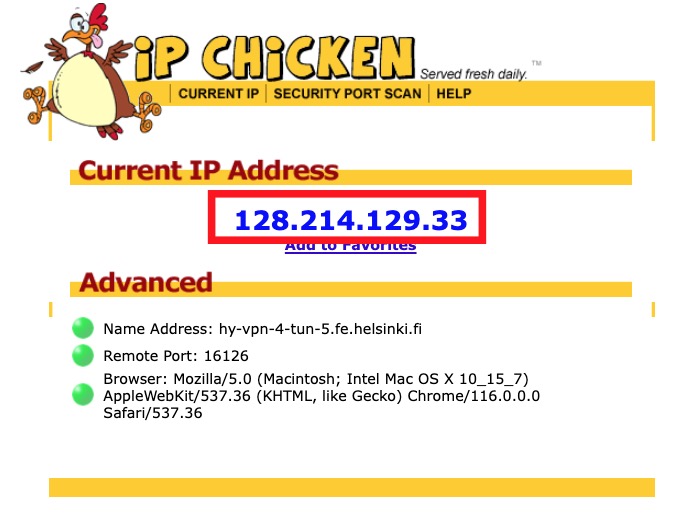
With your browser, go to a service that displays the visitor’s details. One such service is https://ipchicken.com/. See, what type of IP address the service reports your connection comes from.
If the IP starts with 128.214 that means you are using the university’s IP address, which is used to identify you as a university user.
See Detailed help tab for more detailed information
Detailed help
Checking functionality
From your workstation
Make sure that the virtual “tap” network adapter used by HY-VPN exists.
The command ifconfig will print on the screen the information of all network adapters available on your computer.
When the HY-VPN works, the list should include the tap0 virtual adapter, which should have an IP address of the university’s network. The IP address is displayed in the details of the tap0 adapter, on the line that begin inet addr:
kayttaja@testikone:/etc/openvpn# ifconfig
tap0 Link encap:Ethernet HWaddr ea:9f:4f:02:c9:d5
inet addr:128.214.182.163 Bcast:128.214.182.255 Mask:255.255.255.128
inet6 addr: fe80::e89f:4fff:fe02:c9d5/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:13 errors:0 dropped:0 overruns:0 frame:0
TX packets:24 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:1819 (1.8 KB) TX bytes:3815 (3.8 KB
The rest of the line should contain a series of numbers that begin with 128.214. If this is not present or the tap0 adapter cannot be found from the list, the service does not working.
In addition, route settings should be in order, meaning the command route should display the following output on your screen:
kayttaja@testikone:/etc/openvpn# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
openvpn1.fe.hel router-151.hels 255.255.255.255 UGH 0 0 0 eth0
128.214.182.128 * 255.255.255.128 U 0 0 0 tap0
128.214.0.0 * 255.255.0.0 U 1 0 0 eth0
link-local * 255.255.0.0 U 1000 0 0 eth0
default hy-ovpn1-1.vpn. 128.0.0.0 UG 0 0 0 tap0
128.0.0.0 hy-ovpn1-1.vpn. 128.0.0.0 UG 0 0 0 tap0
default router-151.hels 0.0.0.0
UG 0 0 0 eth0
The output should include routes required by openvpn. These have been highlighted in the above image. If you cannot find them, make sure that the configuration file /etc/openvpn/openvpn.conf includes the definition “redirect-gateway def1“. Add this line, if it is not included in the file.
With a browser
With your browser, go to a service that displays the visitor’s details. One such service is www.ipchicken.com. See, what type of IP address the service reports your connection comes from.
If the IP starts with 128.214 that means you are using the university’s IP address, which is used to identify you as a university user.
Firewall
Unless firewall rules are added, the firewall may block openvpn’s traffic causing it not to work. The firewall must allow openvpn traffic and forwarding.
If you are unsure about firewall rules, you can check that openvpn works by disabling the firewall. After doing this, start openvpn and see if it works. If everything works as expected, turn the firewall on without quitting openvpn. If the firewall rules that allow openvpn to work are in order, everything should keep working as normal.
The following lines in the iptables firewall ensure that openvpn works:
- iptables -A INPUT -p udp --dport 1194 -j ACCEPT
- iptables -A INPUT -i tap+ -j ACCEPT
- iptables -A FORWARD -i tap+ -j ACCEPT
Support services for using and in case of errors
If the above instructions are not sufficient to solve your problem, please contact Helpdesk. Describe the problem in as much detail as possible and attach an openvpn logfile and output from the ifconfig and route commands. Without all of this information, it is very difficult to pinpoint the error and suggest any fixes.
Video instruction
Give feedback
The instructions site of the University of Helsinki's IT Helpdesk helps you with IT-related issues related to your work. Let us know how we can improve our instructions. We greatly appreciate your feedback!
How would you improve these instructions?