Many university email users receive phishing messages on a regular basis. The purpose of these scams is to persuade people into disclosing their user account information, passwords, or e.g. their credit card information.
Quick help
Detailed help
An exemplary caption of a phishing email is found below:
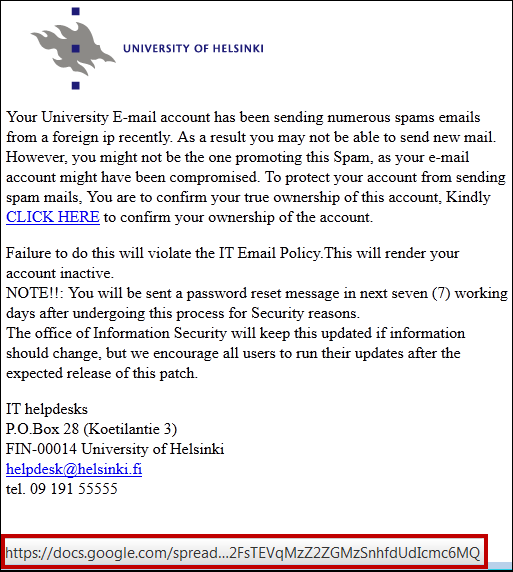
How to identify a phishing message
- The University IT staff or Helpdesk will NEVER ask for your user account information via email! Messages prompting you for your password are ALWAYS scams.
- Some of the currently circulating phishing messages contain a link to a page where the user should allegedly check their user information or update it. Often these messages will claim that the user's email quota is full, or that failure to fill in the requested information will lead to the inactivation of the user's email account.
- Check the target address of the link: Hover your cursor over the link (without clicking it!). The address will be shown in the bottom part of the screen. If the address does not seem authentic, the message is most probably a fake.
- If you have any reason to doubt the authenticity of a message, don't open any links it may contain. Please ask the Helpdesk instead!
- The University does NOT send its users links to pages asking for user information or passwords. .
- If you are targeted by phishing messages, please contact the University of Helsinki IT Helpdesk. Only report attempts to acquire your password!
- Never let anyone else use your user account or password!
Consequences of phishing
Phishing may have serious consequences. Phishers almost always try to scam you for money or otherwise make a profit from the usernames they have phished. Online criminals have used phished usernames at least for the following purposes:
- Sales of usernames – university usernames make it possible to access large amounts of data.
- Money transfer scams by impersonating the owner of a phished username.
- Identity thefts using the information accessible with the username.
- Hijacking of e-mail boxes and blackmailing in order to restore them.
- Spamming, resulting in the sender’s address being put in the recipient’s blocklist.
If you suspect your personal information may have been compromised
- Change your password immediately and contact the Helpdesk
See instructions: Changing your password
Avoiding online scams
Student’s digital skills contain a comprehensive information package of tricks used by scammers.
Reporting junk mail
With the help of these instructions, you can report junk mail
Video instruction
Give feedback
The instructions site of the University of Helsinki's IT Helpdesk helps you with IT-related issues related to your work. Let us know how we can improve our instructions. We greatly appreciate your feedback!
How would you improve these instructions?