Majordomo is one of University's email list applications. The difference between Majordomo and other lists like Microsoft 365 is that external addresses can be added to the list through Majordomo. This guide describes the tasks of the administrator (owner).
At the University, email lists are primarily maintained using the MajorCool software which allows you to edit the list's recipients, approve messages sent to a restricted list for delivery and change the list's configuration.
Please take this into account when designing mailing lists:
- Majordomo lists can be subscribed to by an IAM group
- A Majordomo list cannot be added to an IAM list.
- If a list is going to include outsiders without a University of Helsinki email address, the Majordomo lists should always be used.
Quick help
About Majordomo
At the University, email lists are primarily maintained using the MajorCool software which allows you to edit the list's recipients, approve messages sent to a restricted list for delivery and change the list's configuration.
- A request to set up a MajorCool mailing list is made via a subscription form.
- The address of MajorCool, the list maintenance tool, is majordomo.helsinki.fi. To use it, you need a University username (use the short form, e.g. "rkeskiva"), the name of the list and its admin password.
- From the MajorCold interface, you can change the maintenance password or administrator.
- To delete an unnecessary mailing list, please contact the IT Helpdesk.
The Majordomo software can be used:
- via the browser-based MajorCool interface.
- by sending commands to Majordomo via email.
Please take this into account when designing mailing lists:
- Majordomo lists can be subscribed to by an IAM group
- A Majordomo list cannot be added to an IAM list.
- If a list is going to include outsiders without a University of Helsinki email address, the Majordomo lists should always be used.
Detailed help
Table of contents
- MajorCool - easy maintenance of mailing lists
- MajorCold - change administrator and administrator password yourself
- Majordomon salasanat
- Listan tilaajien lisääminen ja poisto
- Tervetuloviestin asettaminen listalle
- Viestien otsikon etuliite
- Suljetun tai avoimen listan asettaminen
- Viestien ylä- ja alatunniste
- Muita postituslistan asetuksia
- Bounce-viestien hyväksyminen sähköpostilistalle
- Majordomon ei-toivottujen sähköpostiviestien torjunta
- Suodatus eli viestien seulominen "kiellettyjen" sanojen varalta
- Postituksen salliminen vain listan tilaajille
- Listan moderointi
- Moderoidun sähköpostilistan viestien hyväksyminen
- Ylläpitäjän vaihto
- Listan poistaminen
MajorCool - easy maintenance of mailing lists
In addition to the Majordomo software, the university offers the browser interface MajorCool to facilitate the use of lists. This interface sends the administration commands to the software on behalf of the user. This facilitates the administration of the list as errors are easy to make when using e-mail commands.
The address of MajorCool is https://majordomo.helsinki.fi/. Using the interface requires a university username plus the name and administration password of the list.
A reply message is sent to the administrator's address for all actions carried out in the MajorCool interface. Administration operations, such as changing the e-mail list password, can be performed in the MajorCold interface.
MajorCold - change administrator and administrator password yourself
You need a VPN connection (e.g. eduVPN) to use the MajorCold tool.
If you see any unused or redundant email lists in your MajorCold view, please request their deletion from IT Helpdesk.
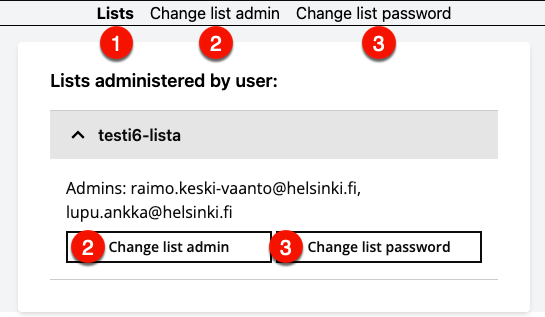
MajorCold is used to change the administrators and password of Majordomo mailing lists. You can log in to MajorCold by using short form of your username (e.g. rkeskiva) at https://majorcold.it.helsinki.fi/.
- When you log in, you will be taken to a page where you will see all the Majordomo mailing lists you are the administrator of, based on your email address. You can return to this view by clicking on the top bar (1) Lists. By clicking on the name of a list (i.e. "test6 list"), you will see the email addresses of the administrators of that list.
- When you click on a specific list or on the top bar:
- (2) Change list admin you will be able to modify the list admins.
- (3) Change list password you can change the list password.
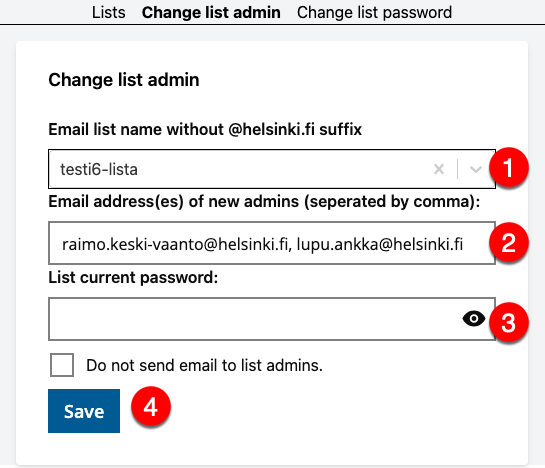
Change list admins
- Select (1) the address of the list the administrators of which you want to change from the drop-down menu. You can also type the name of the list in the text field (list name without the @helsinki.fi ending, i.e. "testi6-lista"). You can change the administrators of a list if you know the list password even if you are not an admin..
- In field (2) "Email address(es) of new admins", enter all the email addresses for which you want list admin rights. If there are more than one administrators, separate the addresses with a comma.
- Enter (3) the current password for the email list and press (4) Save. The change will send an email to both new and old list admins, but you can choose to prevent this by selecting Do not send email to list admins.
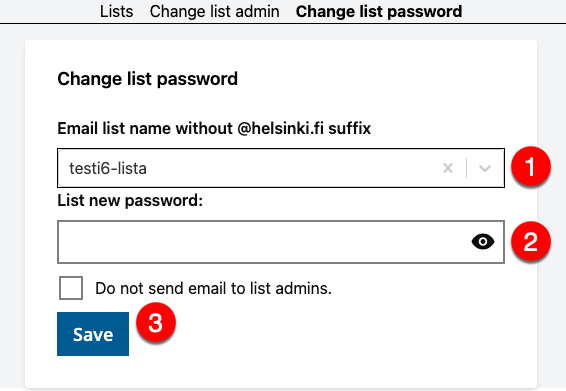
Change the list password
-
Select (1) the address of the list the password of which you wish to change from the drop down menu (list name without the @helsinki.fi ending). You can also type the name of the list in the text field (list name without the @helsinki.fi ending, i.e. "testi6-lista").
-
Enter (2) the new password for the mailing list in the List new password field.
-
Press (3) Save. An email will be sent to the administrators about the change, which you can prevent by selecting Do not send email to list admins.
Majordomon salasanat
Majordomo-palvelussa on käytössä kaksi erillistä salasanaa.
- Tärkein salasana on ns. ylläpitosalasana, jonka voi vaihtaa MajorCold-palvelussa.
- Yksittäiselle listalle voi asettaa vielä erillisen hyväksymissalasanan, eli approve_passwd.
Salasanat on syytä vaihtaa ajoittain tietoturvasyistä. Ainakin silloin, jos (hyväksymis)salasana karkaa vahingossa esimerkiksi listalle. Myös listan ylläpitäjän vaihtuessa ylläpitosalasana on hyvä vaihtaa.
Approve_passwd
Sähköpostilistan asetustiedostossa pitää olla asetettuna approve_passwd. Tämä asetetaan seuraavasti:
- Siirry sivulle https://majordomo.helsinki.fi
- Kirjaudu sisään omalla käyttäjätunnuksellasi ja -salasanallasi
- Kirjoita listan nimi kohtaan List Name (ilman lainausmerkkejä ja nimen @helsinki.fi-osaa)
- Kirjoita listan ylläpitosalasana kohtaan Admin Password
- Valitse kohdasta Modify what? vaihtoehto Configuration Options
- Valitse sivun yläosan pudotusvalikosta All keywords
- Etsi kohta approve passwd, ja kirjoita siihen joku sopiva salasana. Voi olla myös sama kuin ylläpitosalasana, joskaan tätä ei suositella, koska sitä käytettäessä huolimattomasti se saattaa karata listalle. Siksi tässä on hyvä olla "vähempiarvoinen" salasana.
- Paina lopuksi Apply-painiketta
- Vastausviesti tulee viereisessä kentässä olevaan osoitteeseen
Approve_passwd:n käyttöä käsitellään ohjeessa BOUNCE-viestien edelleenlähetys listalle.
Listan tilaajien lisääminen ja poisto
MajorCool-liittymällä
- Siirry sivulle https://majordomo.helsinki.fi
- Kirjaudu sisään omalla tunnuksellasi ja salasanallasi
- Kirjoita listan nimi kohtaan List Name (ilman lainausmerkkejä ja nimen @helsinki.fi-osaa)
- Kirjoita listan ylläpitosalasana kohtaan Admin Password
- Valitse kohdasta Modify What? vaihtoehto List Subscribers
- Lisää ja poista osoitteita tarpeen mukaan alle avautuvasta kentästä
- Paina lopuksi Apply-painiketta.
- Vastausviesti tulee viereisessä kentässä olevaan osoitteeseen
Huomioi osoitelistaa muokatessasi
- Varmista osoitteiden oikeinkirjoitus. Käytä osoitteista täydellisiä muotoja (ei esimerkiksi pelkkiä käyttäjätunnuksia).
- Huom! Vain yksi osoite per rivi. Älä jätä tyhjiä rivejä osoitteiden väleihin.
Sähköpostitse
Majordomo ei osaa tulkita html-muotoisia viestejä. Varmista sähköpostiohjelman asetuksista, että viesti lähtee plain text -muodossa.
Jos hallinnoit listan jäseniä sähköpostin välityksellä,
- voit liittää jäseniä subscribe-komennolla: approve listansalasana subscribe listan-nimi joku.osoite@helsinki.fi
- voit poistaa unsubscribe-komennolla: approve listansalasana unsubscribe listan-nimi joku.osoite@helsinki.fi
Samassa sähköpostiviestissä voit sekä lisätä että poistaa jäseniä. Esimerkki, jossa lisätään kaksi ja poistetaan yksi jäsen:
approve listansalasana subscribe listan-nimi joku.osoite@helsinki.fi
approve listansalasana subscribe listan-nimi toinen.osoite@helsinki.fi
approve listansalasana unsubscribe listan-nimi kolmas.osoite@muualla.fi
Tervetuloviestin asettaminen listalle
Voit halutessasi asettaa uusille liittyville listan jäsenille lähetettävän tervetuloviestin. Tämä teksti liitetään Majordomon oman lyhyen tervetuloviestin perään.
Viestissä voidaan kertoa esimerkiksi minkä tyyppiselle listalle käyttäjä on juuri liittynyt, onko kyse tiedotus- vai keskustelulistasta vai molemmista, keneen otetaan yhteyttä ongelmatilanteissa (owner-listan-nimi@helsinki.fi) ja miten listalta erotaan.
- Siirry sivulle https://majordomo.helsinki.fi
- Kirjaudu sisään omalla tunnuksellasi ja salasanallasi
- Kirjoita listan nimi kohtaan List Name (ilman lainausmerkkejä ja nimen @helsinki.fi-osaa)
- Kirjoita listan ylläpitosalasana kohtaan Admin Password
- Valitse kohdasta Modify what? vaihtoehto Configuration Options
- Tarkista, että kohdassa welcome on valittuna yes
- Ellei ole, valitse yes ja paina Apply-painiketta
- Jos on, valitse alhaalta 'Info' File ja paina Modify-painiketta
- Kirjoita vapaamuotoinen tekstisi kenttään
- Paina lopuksi Apply-painiketta
- Vastausviesti tulee viereisessä kentässä olevaan osoitteeseen
Mikäli tiedät, että kohta welcome on oikein, voit muuttaa tervetuloviestiä myös Majorcoolin etusivulta valitsemalla Modify What? -kohdasta List Info File.
Viestien otsikon etuliite
Listan tilaajille voi olla hyödyllistä nähdä jo viestin otsikosta, että se on tullut tietyltä sähköpostilistalta. Voit määrittää tekstin, joka liitetään jokaisen viestin otsikon alkuun automaattisesti.
Tekstinpätkä määritetään muokkaamalla listan asetuksista kohtaa subject prefix. Kirjoita siihen joku kuvaava etuliite, vaikkapa [listan-nimi].
Tätä asetusta muokataan MajorCoolilla näin:
- Siirry sivulle https://majordomo.helsinki.fi
- Kirjaudu sisään omalla tunnuksellasi ja salasanallasi
- Kirjoita listan nimi kohtaan List Name (ilman lainausmerkkejä ja nimen @helsinki.fi-osaa)
- Kirjoita listan ylläpitosalasana kohtaan Admin Password
- Valitse kohdasta Modify what? vaihtoehto Configuration Options
- Valitse sivun yläosan pudotusvalikosta All keywords
- Etsi kohta subject prefix ja kirjoita siihen haluamasi otsikon etuliite
- Paina lopuksi Apply-painiketta
- Vastausviesti tulee viereisessä kentässä olevaan osoitteeseen
Suljetun tai avoimen listan asettaminen
Sähköpostilistoille liittymisen rajoituksia voidaan muuttaa subscribe policy -asetuksella.
Vaihtoehtoina ovat: open, closed ja auto:
- open on avoin, jolla kuka tahansa voi liittyä
- closed on suljettu lista. Vain ylläpitäjä voi liittää uusia osoitteita. Kaikki muut listalle liittymiset tulevat ylläpitäjän hyväksyttäväksi
- auto-asetuksella kuka hyvänsä voi lisätä kenet hyvänsä listalle, vaikka pilanpäiten.
Vaihtoehdolla auto+confirm osoitteeseen, jota ollaan lisäämässä listalle, lähetetään asiasta varmistusviesti, jolla hän voi hyväksyä tai hylätä liittymisen.
Oletusarvoisesti uudella listalla subscribe_policy on open+confirm, eli kuka tahansa voi liittyä listalle, mutta saa siitä varmistusviestin itselleen.
MajorCool-liittymällä asetusta muutetaan seuraavasti:
- Siirry sivulle https://majordomo.helsinki.fi
- Kirjaudu sisään omalla tunnuksellasi ja salasanallasi
- Kirjoita listan nimi kohtaan List Name (ilman lainausmerkkejä ja nimen @helsinki.fi-osaa)
- Kirjoita listan ylläpitosalasana kohtaan Admin Password
- Valitse kohdasta Modify what? vaihtoehto Configuration Options
- Etsi kohta subscribe policy ja valitse haluamasi vaihtoehto
- Paina lopuksi Apply-painiketta
- Vastausviesti tulee viereisessä kentässä olevaan osoitteeseen
Viestien ylä- ja alatunniste
Usein sähköpostilistan viestien alkuun tai loppuun halutaan lisätä tunniste, joka kertoo esimerkiksi mikä tai millainen lista on kyseessä tai ohjeistaa eroamaan listalta.
Tätä asetusta muokataan MajorCoolilla näin:
- Siirry sivulle https://majordomo.helsinki.fi
- Kirjaudu sisään omalla tunnuksellasi ja salasanallasi
- Kirjoita listan nimi kohtaan List Name (ilman lainausmerkkejä ja nimen @helsinki.fi-osaa)
- Kirjoita listan ylläpitosalasana kohtaan Admin Password
- Valitse kohdasta Modify what? vaihtoehto Configuration Options
- Etsi kohta message fronter tai message footer ja kirjoita niihin haluamasi ala- tai ylätunniste
- Paina lopuksi Apply-painiketta
- Vastausviesti tulee viereisessä kentässä olevaan osoitteeseen
Esimerkki alatunnisteesta:
_________________________________________________________
Tämä on humppalogian laitoksen tiedotus- ja keskustelulista. Ongelmatilanteissa lähetä postia osoitteeseen owner-humppa-lista@helsinki.fi WWW-sivumme ovat osoitteessa https://www.helsinki.fi.invalid/jarj/humppaa/. Sivuilla on listaltaeroamisohjeet. Älä lähetä eropyyntöjä listalle!
_________________________________________________________
Muita postituslistan asetuksia
Seuraavassa joitakin muita olennaisia asetuksia. Kaikkia näitä muutetaan MajorCoolilla suunnilleen samalla tavalla:
- Siirry sivulle https://majordomo.helsinki.fi
- Kirjaudu sisään omalla tunnuksellasi ja salasanallasi
- Kirjoita listan nimi kohtaan List Name (ilman lainausmerkkejä ja nimen @helsinki.fi-osaa)
- Kirjoita listan ylläpitosalasana kohtaan Admin Password
- Valitse kohdasta Modify what? vaihtoehto Configuration Options
- Valitse sivun yläosan pudotusvalikosta All keywords
- Etsi haluamasi asetukset
- Tee haluamasi muutokset, lue kuitenkin MajorCoolin ohjetekstit
- Paina lopuksi Apply-painiketta
- Vastausviesti tulee viereisessä kentässä olevaan osoitteeseen
advertise
- Tällä voidaan rajoittaa sitä, kenelle lista näkyy Majordomon lists-komennolla. Tähän voidaan laittaa säännöllinen lauseke, joka tunnistaa ne sähköpostiosoitteet, joille listan halutaan näkyvän. Esim. kaikille suomalaisille (regexp on tällöin /*.fi/).
lists-komento ei ole käytössä yliopistossa väärinkäytön takia. - Oletusarvo + rajoitukset: OFF
announcements
- Lähetetäänkö listan ylläpitäjälle viestejä eroamisista ja liittymisistä. Kannattaa pitää käytössä väärinkäytösten estämiseksi.
- Oletusarvo + rajoitukset: yes
approve_passwd
- Salasana, jolla voi edelleenlähettää BOUNCE-viestit listalle (Katso ohje Bounce-viestien edelleenlähetykseen). Tässä pitää olla joku arvo, muuten Majordomo ei toimi oikein. Vaihda oletusarvo muuksi mahdollisimman pian.
- Voi olla myös sama kuin ylläpitosalasana, joskaan tätä ei suositella, koska sitä käytettäessä huolimattomasti se saattaa karata listalle. Siksi tässä on hyvä olla "vähempiarvoinen" salasana.
Lue lisää kohdasta Majordomon salasanat. - Oletusarvo + rajoitukset: listan-nimi.pass
description
- Listan kuvaus lists-komentoa varten.
- Oletusarvo + rajoitukset: OFF. Suurin sallittu pituus 50 merkkiä.
info_access
- jos closed, info-komento toimii vain listan jäsenille
- Oletusarvo + rajoitukset: open
maxlength
- Listan viestien suurin sallittu koko.
- Oletusarvo + rajoitukset: 40000 merkkiä.
Huom! Kokoa ei kannata kasvattaa kovin paljon varsinkaan isoilla listoilla, koska isot viestit tukkivat postijärjestelmät. Postijärjestelmissä voi myös olla kokorajoituksia viesteille.
message_footer
- Jokaisen viestin loppuun liitettävä teksti (Lue lisää kappaleesta Viestien ylä- ja alatunnisteet).
- Oletusarvo + rajoitukset: NONE
message_fronter
- Jokaisen viestin alkuun liitettävä teksti (Lue lisää kappaleesta Viestien ylä- ja alatunnisteet).
- Oletusarvo + rajoitukset: NONE
message_headers
- Jokaisen lähtevän viestin otsikkotietoihin liitettävä otsakerivi.
- Oletusarvo + rajoitukset: NONE. Muodon pitää olla X-otsikon-nimi: otsikkokentän arvo
moderate
- Listan moderointitila. Moderoidussa listassa kaikki viestit menevät listan ylläpitäjälle hyväksyttäväksi ennen listalle lähettämistä.
- Oletusarvo + rajoitukset: NONE
noadvertise
- Säännöllinen lauseke, johon sopiville sähköpostiosoitteille listan nimi ei näy lists-komennolla.
lists-komento ei ole käytössä yliopistossa väärinkäytön takia. - Oletusarvo + rajoitukset: NONE. Vrt. muuttuja advertise. Jos käyttäjä sopii sekä noadvertise-lausekkeeseen että advertise-lausekkeeseen, ensin mainittu on voimakkaampi eikä listaa näytetä.
reply_to
- Kenelle vastaus listalta tulevaan viestiin lähetetään: viestin kirjoittajalle ($SENDER) vai listalle ($LIST).
- Oletusarvo + rajoitukset: $SENDER
restrict_post
- Tiedosto, jossa on listattu osoitteet, joista pystyy lähettämään listalle postia.
- Oletusarvo + rajoitukset: NONE
subject_prefix
- Sana tai lause, joka lisätään jokaisen listaviestin otsikon alkuun, mikä helpottaa esim. viestien lajittelua. Arvo voi olla esimerkiksi $LIST. Katso kappale Viestien otsikon etuviite.
subscribe_policy
- Listalle liittymisen politiikka:
- auto: kuka tahansa saa lisätä listalle kenet tahansa
- open: kuka tahansa saa lisätä itsensä listalle
- closed: vain ylläpitäjä voi suorittaa lisäyksen
- confirm: edellä mainittuihin voi liittää tämän piirteen, jolloin liitettävä henkilölle lähetään varmistusviesti, ja kiusalla tehdyt liittämiset estyvät.
Ylläpitäjälle lähetettävä tieto liittymisistä ja eroamisista riippuu asetuksesta announcements.
taboo_body
- Viesti, jonka tekstiosassa on taboo_body-asetuksessa määritelty merkkijono, ei pääse suoraan listalle, vaan se lähetetään ylläpitäjälle hyväksyttäväksi. Syntaksi on perlin regexp. Katso kohta Ei-toivottujen viestien torjunta.
- Oletusarvo + rajoitukset: NONE
taboo_headers
- Kuten taboo_body, mutta tekstiä etsitään viestien otsikkotiedoista.
- Oletusarvo + rajoitukset: NONE
unsubscribe_policy
- Saako listalta erota omin neuvoin. Vertaa subscribe_policy.
- Oletusarvo + rajoitukset: open
Bounce-viestien hyväksyminen sähköpostilistalle
Listalle lähetetyt viestit voivat tulla listan ylläpitäjälle hyväksyttäväksi esimerkiksi, kun
- viesti täsmää listan omiin tai Majordomon yleisiin suodattimiin
- viestin on lähettänyt listan ulkopuolinen lähettäjä, kun listalle postittaminen on varattu vain sen tilaajille
- lista on moderoitu, jolloin kaikki viestit kulkevat ylläpitäjän kautta
- viesti on liian iso (oletus on 40 000 merkkiä)
- viestin otsaketiedot ovat poikkeuksellisen pitkät (useimmiten pitkä vastaanottajalista)
BOUNCE-viestin otsikko kertoo, mistä oli kyse, esimerkiksi
- BOUNCE listan-nimi@helsinki.fi: Non-member submission from [joku.tyyppi@hellsinki.if]
- BOUNCE listan-nimi@helsinki.fi: taboo body match "/\.pif/" at line 7
- BOUNCE listan-nimi@helsinki.fi: global taboo header: /^subject:\s*FREE/i
- BOUNCE listan-nimi@helsinki.fi: taboo header: m%content-type:.*text/html%i
- BOUNCE listan-nimi@helsinki.fi: Message too long (>40000 chars)
- BOUNCE listan-nimi@helsinki.fi: Approval required
- BOUNCE listan-nimi@helsinki.fi: Header field too long (>3072)
BOUNCE-viesti tulee yleensä osoitteeseen listan-nimi-approval@helsinki.fi. Viesti hyväksytään lisäämällä viestin otsakkeiden ensimmäiseksi riviksi
Approved: salasana
ja lähettämällä viesti edelleen listan osoitteeseen. Kun viestissä on Approved-otsake ja oikea salasana, se pääsee suodattimien ohi listalle.
Tähän on kaksi tapaa:
- Hyväksyntä käsityönä postiohjelmassa
- Approve-komennon käyttö unix-postiohjelmissa
Hyväksyntä käsityönä
BOUNCE-viestin tekstiosan alkuun tulee näkyviin alkuperäisen listalle tarkoitetun viestin otsaketiedot. Näiden edelle viestin tekstiosaan lisätään edellä mainittu Approve-rivi välittömästi ennen alkuperäisiä otsakkeita ilman tyhjää riviä. Menettelytapa on sama riippumatta BOUNCE-viestin syystä.
Vastaavalla tavalla liittämällä Approve-rivi viestin alkuun voit lähettää postia ylläpitäjänä moderoidulle listalle, ilman että sitä tarvitsee enää erikseen hyväksyä. Tässä tilanteessa Approve-rivin ja tekstin välissä on oltava tyhjä rivi.
Erityisohjeet vanhempien sähköpostiohjelmien käyttäjille
Kenttä, jossa lähetettävää viestiä muokataan, on sen verran kapea, että viestin pitkien rivien loppuosat saattavat siirtyä seuraavalle riville. Erityisesti tämä koskee pitkiä otsaketietoja.
Pitkät rivit täytyy poistaa tai muokata lyhyemmiksi. Seuraavalle riville siirtyneitä tekstejä on hieman hankala erottaa tavallisista tekstiriveistä, joten kannattaa olla tarkkana.
Yleensä ongelma koskee pitkiä monirivisiä Received-otsakkeita (viestien välitystietoja) ja Subject-riviä. Received-rivit on syytä poistaa kokonaan, niitä ei pidä muokata. Majordomo-ohjelma tulkitsee vialliset otsakerivit väärin ja listalle pääsee luettavaksi tekstisotkua, jota ei kukaan halua lukea.
Kannattaa myös huomata, että sähköpostiohjelma saattaa lisätä viestin loppuun automaattisesti tekstejä kuten "Edelleenlähetetty viesti päättyy" ja mahdollisesti allekirjoituksesi. Muista poistaa myös nämä.
Hyväksyntä approve-komennolla
Listan ylläpitäjä voi käyttää mitä tahansa postiohjelmaa, kunhan siinä on mahdollisuus lähettää plain text -muodossa.
Aluksi luodaan kotihakemistoon .majordomo-tiedosto (huomaa piste alussa).
Lisätään tiedostoon tekstirivi
listan-nimi salasana majordomo@helsinki.fi
Jos ylläpidettävän on useampia listoja, jokainen lista pitää olla omalla rivillään.
Etsi postiohjelman viestilistasta käsiteltävä viesti ja paina viestin kohdalla | -merkkiä (pystyviiva, näppäimistöltä AltGr + >), kirjoita approve ja paina Enter-näppäintä. Majordomon approve-komento huolehtii viestin siivoamisen ja hyväksynnän.
Mahdollisia ongelmia
Jos viestien hyväksymisessä on ongelmia varmista, että listan asetuksissa on asetettuna approve_passwd.
Katso ohje salasanan asettamiseksi Muita asetuksia -kohdasta.
Lue lisää salasanoista kohdasta Majordomon salasanat.
Tämän puuttuessa, koko Approved:-otsake salasanoineen ja myös muut otsaketiedot välittyvät kaikille listalaisille.
- Salasana on kirjoitettu täsmälleen oikein. Tarkoitukseen käy sekä listan salasana että approve_passwd-salasana, mutta riskien välttämiseksi käytä jälkimmäistä.
- Käyttämäsi sähköpostiohjelma ei katkaise liian pitkiä rivejä.
- Lähetit hyväksytyn viestin listalle osoitteeseen listan-nimi@helsinki.fi, etkä Majordomolle osoitteeseen majordomo@helsinki.fi.
- Approved: salasana on viestisi ensimmäinen rivi.
- Approved-sana alkaa isolla A-kirjaimella ja muut kirjaimet ovat pieniä, sana alkaa täsmälleen rivin alusta ja kaksoispisteen jälkeen on välilyönti.
- Approved-rivin edellä tai jäljessä ei ole tyhjiä rivejä.
Majordomon ei-toivottujen sähköpostiviestien torjunta
Majordomo tarjoaa muutamia kevyehköjä keinoja roskapostin torjuntaan.
Kaikilla on hyvät ja huonot puolensa ja käyttötarkoituksensa. Mikäli listan ylläpitäjä hoitaa tehtäväänsä passiivisesti, näiden käytössä kannattaa olla maltillinen. Alla taulukko torjuntakeinojen eduista ja haitoista. Keskitetyn roskapostintunnistuksen avulla myös sähköpostilistoille pyrkivää roskapostia voidaan suodattaa helposti.
Vaihtoehtoisia torjuntatapoja:
Suodatus avainsanojen perusteella
Plussat
- melko toimiva yhdistettynä yliopiston keskitettyyn roskapostintunnistukseen
- ainoa mahdollinen täysin avoimella keskustelulistalla
- joustava: suodatuksen tiukkuus ylläpitäjän määriteltävissä
- myös mahdolliset listahäiriköt tehokkaasti kuriin
Miinukset
- ei aukoton, roskapostittajat ovat ovelia ja kiertävät suojauksia
- saattaa olla ylläpitäjälle työläs
Suljettu postitus
Plussat
- vain listalaiset lähettävät: ei roskapostia
- sopii hyvin tiedotuslistoille, välttävästi keskustelulistoille
Miinukset
- kaikki eivät lähetä postia samasta osoitteesta kuin millä ovat listan tilaajia: viesti tulee ylläpitäjälle hyväksyttäväksi
- em. syystä on ylläpitäjälle työläs, jos lista on aktiivinen
Listan moderointi
Plussat
- kaikki viestit tarkastetaan: ei roskapostia
- sopii melko hiljaiselle tiedotuslistalle
Miinukset
- ei sovi keskustelulistalle
- täydellinen ylläpitäjän kontrolloima sensuuri
- ylläpitäjälle työläs: hänen on oltava valmiina tai tiedettävä etukäteen viestistä, jotta se pääsisi listalle
Kaikilla torjuntatavoilla ei-toivottu viesti lähetetään listan ylläpitäjälle, joka harkintansa mukaan hyväksyy viestin listalle. Lue tästä lisää BOUNCE-viestien edelleenlähetys listalle -kappaleesta.
Suodatus eli viestien seulominen "kiellettyjen" sanojen varalta
Majordomon suodatuksessa viesteistä etsitään ylläpitäjän määrittelemiä merkkijonoja (sanoja). Jos määritelty sana löytyy, viesti lähetetään ylläpitäjälle ns. BOUNCE-viestinä. Ylläpitäjä hyväksyy tai hylkää viestin. Hyväksytty viesti ohjataan listalle.
Avainsanat määritellään kahteen listaan: taboo body ja taboo headers
- taboo body -listan sanoja etsitään viestin tekstiosasta.
- taboo headers -listan sanoja haetaan viestin otsaketiedoista. Näitä ovat mm. From-, To- ja Subject-kentät sekä viestin välitystiedot.
Avainsanalistat määritellään seuraavasti:
- Siirry sivulle https://majordomo.helsinki.fi
- Kirjaudu sisään omalla käyttäjätunnuksellasi ja -salasanallasi
- Kirjoita listan nimi kohtaan List Name (ilman lainausmerkkejä ja nimen @helsinki.fi-osaa)
- Kirjoita listan ylläpitosalasana kohtaan Admin Password
- Valitse kohdasta Modify what? vaihtoehto Configuration Options
- Valitse sivun yläosan pudotusvalikosta All keywords
- Etsi kohdat taboo body tai taboo headers ja lisää niihin haluamasi lausekkeet
- Paina lopuksi Apply-painiketta
- Vastausviesti tulee viereisessä kentässä olevaan osoitteeseen
Yliopiston keskitetty roskapostin tunnistus parantaa Majordomon suodattimien kykyä estää roskaviestien pääsy listoille. Liittämällä taboo_headers-listaa avainsana X-HY-Spam-Status löydetään kaikki mahdolliseksi roskapostiksi tunnistetut viestit (ks. seuraavan luettelon ensimmäinen esimerkki).
Esimerkkejä Majordomon taboo-lausekkeista
taboo headers
- /^X-HY-Spam-Status/ Mahdolliseksi roskapostiksi tunnistetut viestit
- /mail\.yahoo\.co\./ Kaikki viestit mail.yahoo.co-osoitteista
- /joku\.pontto\@jossa\.kin/ Häirikköjen sähköpostiosoitteet
- /^subject:\s*virgin/i
- /^subject:\s*teen/i Tyypilliset pornopostit
taboo body
- /not a spam/i
/not spam/i Roskapostittajat mainostavat usein, ettei viesti ole roskapostia (spam) - /opt-in/i
/opt-out/i Roskapostittajat tarjoavat usein (valheellisesti) mahdollisuutta lopettaa asiattomat lähetykset. - /adult/
- /MAKE\sMONEY/
- /investment/i
- /viagra/i
Hyväksi havaittuja avainsanoja, joista osa toimii myös taboo_headers-estolistassa. Kannattaa kuitenkin varoa liian yleisiä sanoja, etteivät asialliset viestit tartu suodattimeen.
- /voitteko.*listaltanne/i Listalta eroamispyynnöt
- /\.(exe|pif|scr)/ Mahdollisesti viruksia sisältävät tiedostotyypit
- /^Content-Transfer-Encoding:\s*base64/i Ainoa keino tarkastaa BASE64-koodatut viestit, joita roskapostittajat ahkerasti käyttävät.
- /\.gif/ /\.jpg/ Tavallisimmat kuvaformaatit. Näitä ei yleensä ole tavallisissa sähköpostiviesteissä.
- //i HTML-koodi ei kuulu sähköposteihin, vaikka monet sitä käyttävät, roskapostittajat lähes poikkeuksetta.
- /content-type:.*text\/html/i HTML-viestien suodattaminen lisää ylläpitäjän työtä, koska asiallisetkin viestit usein sisältävät HTML-kieltä. Tätä voi käyttää myös taboo_headers-estolistassa.
Lisäyksiä voi tehdä tarpeen mukaan.
Teknisiä huomioita
- avainsanat esitetään kukin omalla rivillään
- jokaisen merkkijonon alussa ja lopussa on yleensä kauttaviivamerkki ( / )
- viimeisen /-merkin jälkeinen i tarkoittaa, ettei kirjainkoosta välitetä (case insensitive). Ilman tätä SPAM ja Spam ovat eri sanoja
- mikäli sanaan sisältyy /-merkki, sen eteen on laitettava kenoviiva-merkki ( \ ), siis näin \/
- \s tarkoittaa välilyöntiä
- piste ( . ) tarkoittaa 'mikä tahansa merkki'
- tähti ( * ) tarkoittaa 'mielivaltainen määrä edeltävää merkkiä', eli \s* on 'mielivaltaisen monta välilyöntiä' ja .* taas on 'mielivaltainen määrä mitä tahansa merkkiä'
- kenoviivamerkkiä ( \ ) voidaan käyttää erikoismerkkien, kuten tähden, pisteen tai kauttaviivan edellä, jolloin niiden erikoismerkitys katoaa
Postituksen salliminen vain listan tilaajille
Postitus estetään listan ulkopuolisilta seuraavasti
- Siirry sivulle https://majordomo.helsinki.fi
- Kirjaudu sisään omalla käyttäjätunnuksellasi ja -salasanallasi
- Kirjoita listan nimi kohtaan List Name (ilman lainausmerkkejä ja nimen @helsinki.fi-osaa)
- Kirjoita listan ylläpitosalasana kohtaan Admin Password
- Valitse kohdasta Modify what? vaihtoehto Configuration Options
- Valitse sivun yläosan pudotusvalikosta All keywords
- Etsi kohta restrict post, kirjoita siihen listan nimi (esim. humppa-lista), varo kirjoitusvirheitä!
- Paina lopuksi Apply-painiketta
- Vastausviesti tulee viereisessä kentässä olevaan osoitteeseen
Näin vain listan tilaajat voivat postittaa listalle, muiden lähettämät viestit kiertävät ylläpitäjän hyväksynnän kautta. Viestien hyväksymisestä lisää luvussa BOUNCE-viestien edelleenlähetys listalle. Katso ohje Bounce-viestien edelleenlähetykseen.
Listan moderointi
Listan moderointi on eräänlaista ennakkosensuuria. Kaikki viestit kiertävät listan ylläpitäjän hyväksynnän kautta. Se on kätevä tapa valvoa kaikkea listalle postittamista, mikäli se on tarpeen.
Listan moderointi asetetaan käyttöön seuraavasti
- Siirry sivulle https://majordomo.helsinki.fi
- Kirjaudu sisään omalla käyttäjätunnuksellasi ja -salasanallasi
- Kirjoita listan nimi kohtaan List Name (ilman lainausmerkkejä ja nimen @helsinki.fi-osaa)
- Kirjoita listan ylläpitosalasana kohtaan Admin Password
- Valitse kohdasta Modify what? vaihtoehto Configuration Options
- Valitse sivun yläosan pudotusvalikosta All keywords
- Etsi kohta moderate ja valitse yes
- Paina lopuksi Apply-painiketta
- Vastausviesti tulee viereisessä kentässä olevaan osoitteeseen
Moderointi vaatii ylläpitäjältä jatkuvaa listan seuraamista, jottei viestien listalle pääsyyn tulisi kohtuuttomia viiveitä. Viestien hyväksymisestä lisää luvussa BOUNCE-viestien edelleenlähetys listalle.
Viestien ennakkohyväksyminen (pre-approve)
Moderoinnissa on myös ylläpitäjän lähettämät viestit joudutaan erikseen hyväksymään listalle. On mahdollista lähettää viestejä moderoinnin ja muiden suodatuskeinojen ohi lisäämällä viestin alkuun rivi
Approved: salasana
Tämä voidaan lisätä
- joko oman viestin ensimmäiseksi riviksi, jonka jälkeen on tultava tyhjä rivi
- tai viestin otsakkeisiin (headers), mikäli postiohjelmasi tukee tätä.
Pine-ohjelma tukee jälkimmäistä mahdollisuutta lisäämällä sana Approved ohjelman asetuksien kohtaan customized-hdrs. Viestiä kirjoitettaessa otsakkeiden kohdalla näppäillään Ctrl+R ja kirjoitetaan salasana.
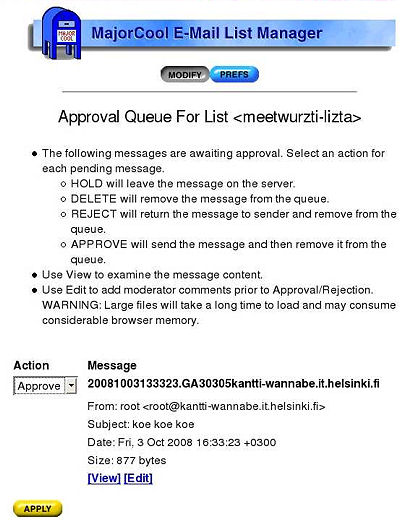
Moderoidun sähköpostilistan viestien hyväksyminen
Moderoidussa sähköpostilistassa ylläpitäjä joutuu hyväksymään kaikki viestit, ennen kuin ne pääsevät jakeluun listalle. Viestin hyväksyminen onnistuu helposti selainpohjaisella MajorCool-ohjelmalla.
- Kirjaudu MajorCool-ohjelmaan osoitteessa https://majordomo.helsinki.fi
- Anna kirjautumisikkunaan yliopiston käyttäjätunnuksesi ja salasanasi
- Anna ylläpitämäsi listan nimi kenttään List Name ja listan ylläpitosalana kenttään Admin Password
- Valitse Approval Queue
- Paina Go-painiketta
- Napsauta tarvittaessa hyväksyttävän viestin otsikkotietojen alta View-linkkiä katsoaksesi viestin sisältöä
- Valitse Action-pudotusvalikosta Approve
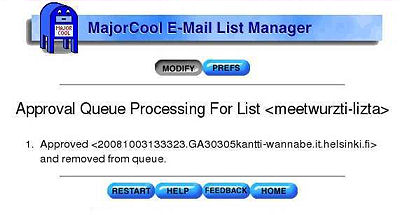
- Paina Apply-painikketta
- Saat lopuksi ilmoituksen viestin onnistuneesta hyväksymisestä
Ylläpitäjän vaihto
Listan ylläpitäjä (owner) voi itse siirtää tehtäviään seuraajalleen MajorCold-sovelluksella. Lue lisää ohjeen kohdasta MajorCold.
Listan poistaminen
Listan voi poistaa vain ylläpito. Ilmoita käyttämättömäksi jääneestä listasta IT-Helpdeskiin (katso yhteydenotto-ohje erillisestä ohjeesta).
Video instruction
Give feedback
The instructions site of the University of Helsinki's IT Helpdesk helps you with IT-related issues related to your work. Let us know how we can improve our instructions. We greatly appreciate your feedback!
How would you improve these instructions?